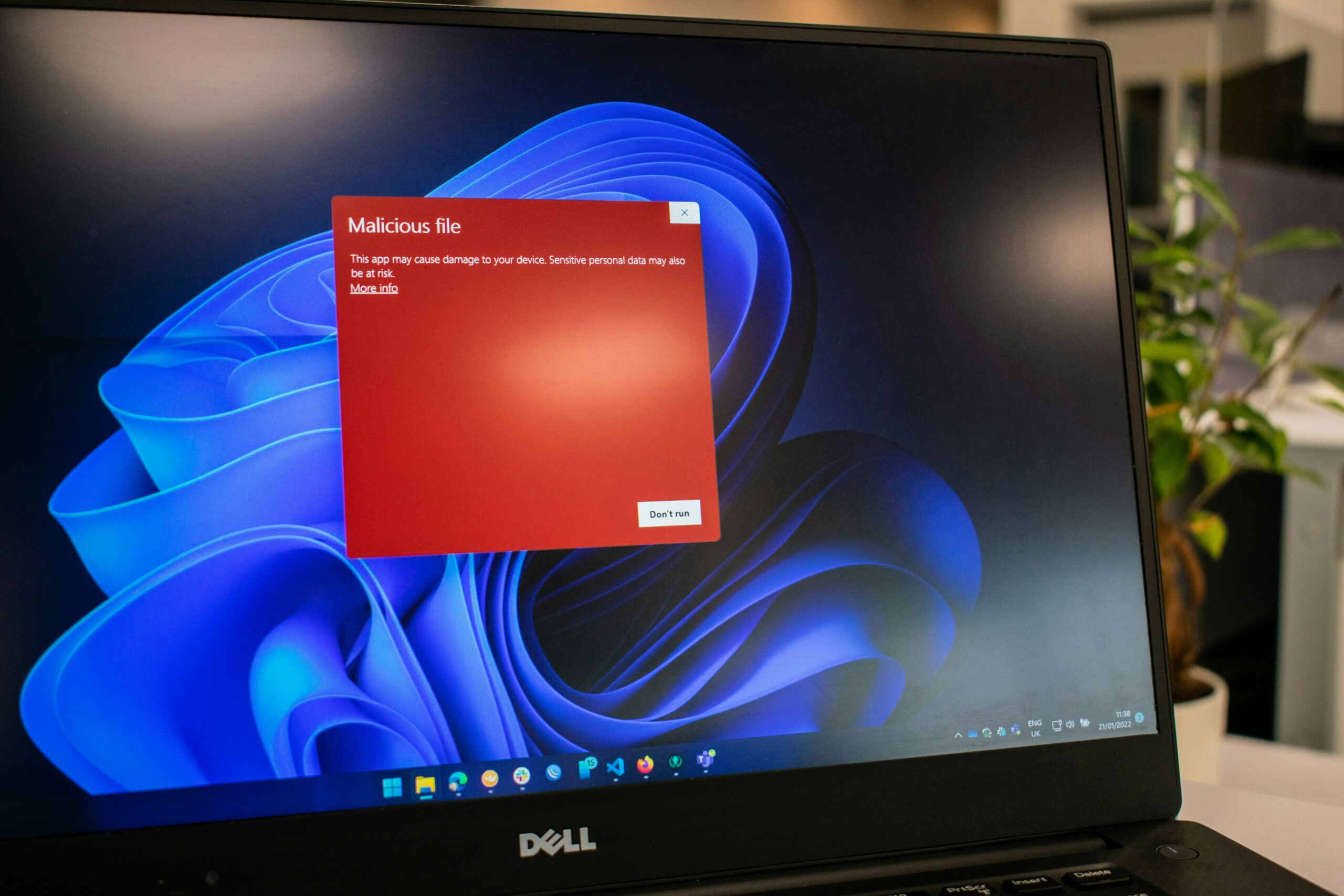
As cyber threats continue to grow in sophistication, the need for proactive measures to safeguard enterprises has never been more critical.Co-hosted with YBhg. Dato’ Ts. Dr Haji Amirudin Bin Abdul Wahab, Chief Executive Officer, CyberSecurity Malaysia and his team, AIBP hosted an exclusive, closed-door workshop, on Building Cyber Resilience, addressing the following themes:
- Mitigating Risks through Proactive Cyber Risk Management and Resilience Strategies
- Leveraging Technologies to Strengthen Cyber Resilience in a Dynamic Threat Landscape
- Governance Frameworks for Data Management and Emerging Technologies
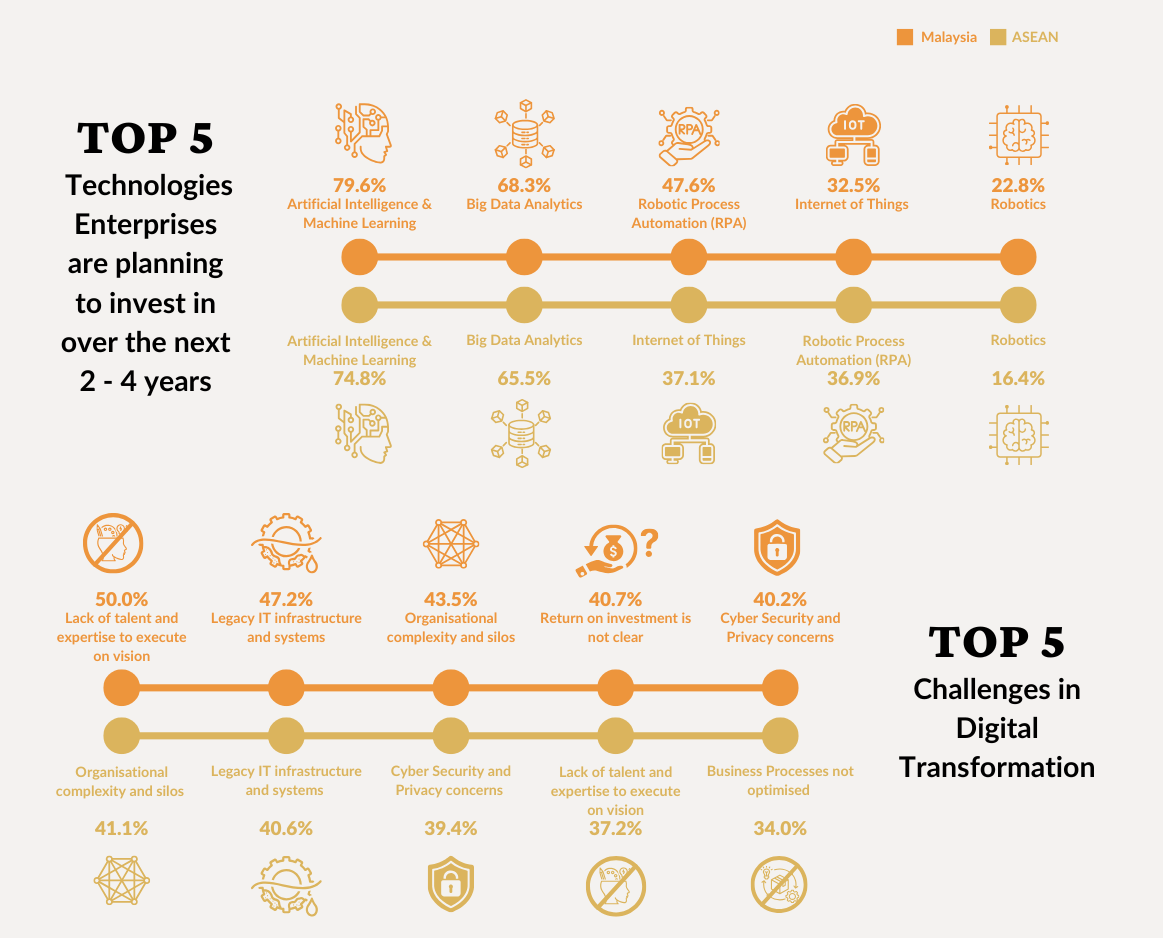
In the recently published AIBP ASEAN Enterprise Innovation Market Overview, cyber security and privacy concerns (40.2%) is one of the top challenges in digital transformation among Malaysian enterprises.
Key Challenges and Strategies
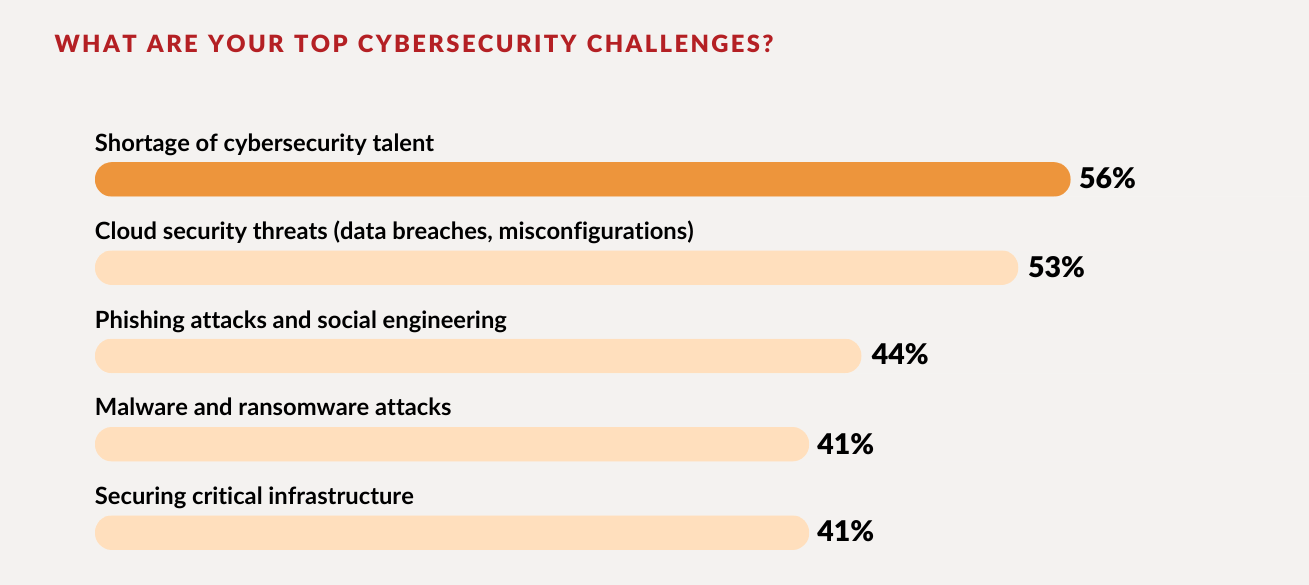
Talent Shortages in Cybersecurity
A live poll with leaders from Malaysian enterprises identified the lack of cybersecurity talent ( voted by 56%) as a critical barrier to effective risk management. Participants emphasised the need for public-private collaboration to attract, develop, and retain talent. Proactive strategies included investments in Security Operations Centres (SOCs) and partnerships with external cybersecurity experts to close the skills gap.
“The Malaysian cybersecurity ecosystem is making commendable strides, particularly with efforts to align security providers with the Cybersecurity Act. However, businesses must evaluate vendors not just at the organisational level but also consider whether the vendor demonstrates strong data governance and maintains skilled in-house talent. Overlooking this can significantly heighten third-party risks for clients.
For instance, in scenarios involving banks or critical infrastructure, relying on security vendors who primarily engage freelancers for penetration testing can pose serious threats. There’s a real risk that sensitive client information could be mishandled—or worse, end up for sale on the Dark Web. It’s crucial to prioritise trust and accountability when choosing security partners.”
Victor Lim, Director of Business Development, softScheck APAC
Complexity of Cloud Security
As businesses increasingly migrate to cloud-based environments, managing cybersecurity has become more complex (as indicated by 53%). Leaders emphasised the need for a comprehensive security fabric that can protect data across multiple platforms and service providers. The discussion highlighted the importance of implementing a hybrid approach, combining on-premises and cloud-based security solutions to create a robust defense against cyber threats.
Standardising Practices for Resilience
A recurring theme throughout the discussion was the urgent need for standardised cybersecurity practices across industries. Participants agreed that collaboration between public and private sectors is crucial for developing effective strategies to combat cyber threats. The recent implementation of the Cyber Security Act 2024 in Malaysia was cited as a significant step towards establishing a unified framework for cyber security governance.
Zero Trust Architecture as a Cornerstone
Adopting zero-trust architecture was underscored as a key proactive strategy. This approach, which assumes no inherent trust and requires continuous verification, aligns well with the evolving cybersecurity landscape. Leaders emphasised the importance of applying zero-trust principles across businesses, especially in managing identities and controls within software-as-a-service (SaaS) ecosystems.
“When you start considering that data is everywhere now that you know your business is moving at a faster rate, how can you apply the architecture framework across your business to ensure that you know you’ve got the right controls in place? When you think about software as a service, identity becomes that sort of core material control that is managed by your organisation. You need to start thinking about how you apply those particular pieces in there. The other aspect of that is, some of the principles that zero trust align well to what organisations are doing today, right? As you sort of shoot and analyse your cyber strategies in terms of target state and how you go about optimising that there, I think that’s going to sort of play a part.”
— Heng Mok, CISO In Residence, Zscaler

Building a Unified and Resilient Ecosystem
As cyber threats continue to evolve, proactive collaboration between industries is crucial. By fostering partnerships, standardising best practices, and adopting cutting-edge technologies, organisations can effectively mitigate risks and enhance resilience. The workshop served as a vital platform for knowledge sharing, bringing together diverse perspectives to address one of the most pressing challenges in today’s digital economy.
The article was first published by ASEAN Innovation Business Platform (AIBP).

 5.0
5.0