Digital transformation promises to deliver new business value but also introduces new security risks that demand equally new and innovative responses. Organizations on a digital transformation journey must make a parallel trip, one that integrates security and risk management into DevOps and Continuous Delivery (CD) processes.
Security professionals need to be participating in DevOps/CD teams, bringing security aspects into the develop-to-deliver process and addressing built-in security capabilities and operational hooks to mitigate risk. Simultaneously, security operations teams gain access to more detailed logs, and deploy Machine Learning (ML) and Artificial Intelligence (AI) techniques to detect abnormal conditions. Overall, the newly integrated DevOps/CD/security processes, combined with new operational technologies, can make a material change in the enterprise’s risk posture. Ultimately, the business needs a single, converged view of technology risk across both operational and security domains.
Plan for digital transformation and security together
As organizations continue their digital transformations, the transformation of security and risk management must be an integral part of that journey. Rather than bolting-on security at the end, organizations should plan for digital transformation and security together, simultaneously.
In fact, the best way to defend against next-generation threats in the digital age is a structured, enterprise-wide risk management strategy with well-defined governance and policies. The ultimate goal is to have resilient systems that can not only withstand cyber attacks, but also carry out mission-critical business operations after an attack.
This is no easy task, as the risk environment is changing quickly. An effective strategy must now address:
- Identity – As the network’s physical perimeter fades, the ability to authenticate the identity of users and devices and to determine their proper level of access to both systems and data becomes essential. Exacerbating this challenge is the exponential growth of mobility, the internet of things (IoT), automated apps and robotic process automation (RPA), and the widening scope of information security to include operational technology (OT) systems. User analytics must now consider both human and machine-generated behavior.
- Continuous compliance – Data-protection and privacy policies such as the European Union’s General Data Protection Regulation (GDPR) are too often addressed with ad-hoc solutions. A superior approach involves building a security and privacy infrastructure that will prepare your organization to meet the demands of evolving policies.
- Incident response – Enterprises are no longer judged simply by whether they get breached, but how they respond to that breach. The public and regulators recognize that risk is prevalent and breaches will happen. What the public and regulators will not accept is sub-optimum breach response. We need robust incident response capabilities that are consistently tested, ensuring that from the board to the legal department, all are prepared to execute professional incident response that minimizes damage.
- Information and asset governance – Data is increasingly mobile. Recent incidents have included not only hostile actors making internal breaches, but supposedly legitimate third parties circumventing protections to access and store bulk client data. Enterprises need a security and privacy model that continually refreshes, moving with the data, and has appropriate self-destruct mechanisms when anomalies are detected.
- Federation – Third parties increasingly need access to corporate networks, creating a serious security challenge. How do you open your network to suppliers, partners and others while still protecting your systems and data?
People, process and technology
As organizations develop an enterprise risk management strategy along with their digital transformation strategy, they can imagine the effort as a highway with three lanes: one for people, another for process, and a third for technology. (See Figure 1.)
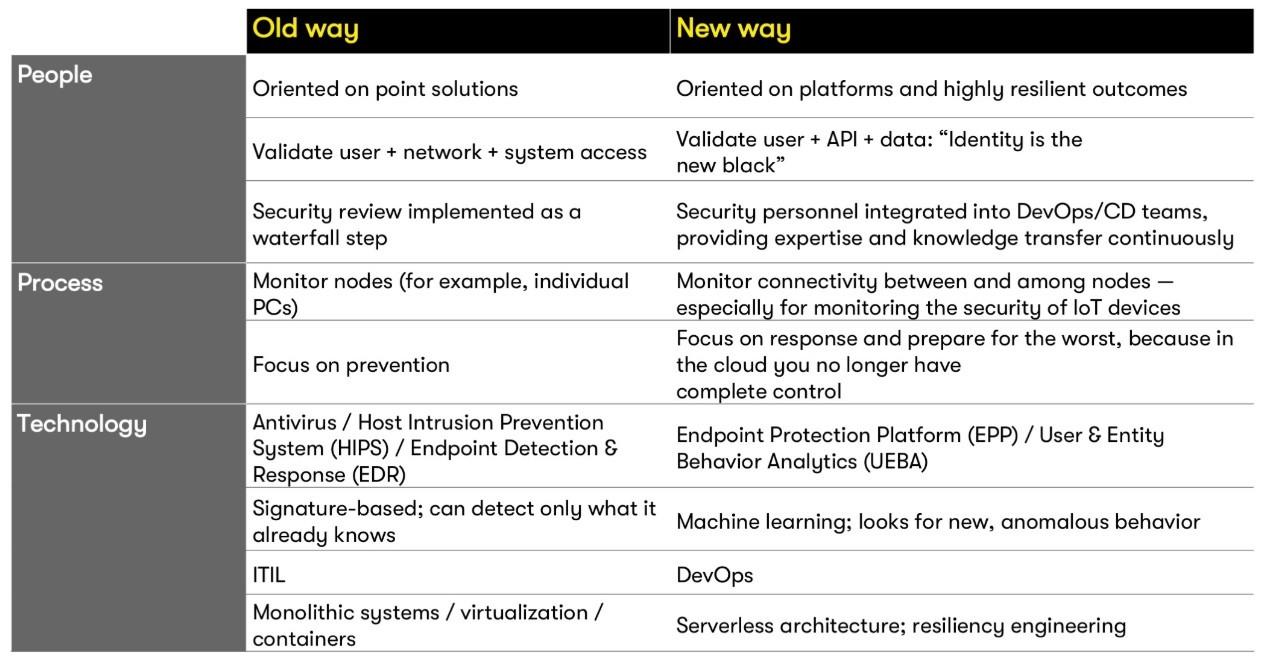
Figure 1. Reducing risk with digital transformation.
Three paths — people, process and technology — are changing quickly.
People in an organization form its culture and are the first line of design and defense for security. For digital transformation to succeed, many organizations will need to transform the culture around risk. Here are a few changes that most likely will be needed:
- DevOps/Continuous Delivery teams become security practitioners. In the near future, security will transition from being a niche skill practiced in near isolation, to being a core capability of developers. This will require a mind-set shift for both security professionals and developers, who have operated in silos for a generation. The first step is to integrate security expertise at the inception of development projects. This will allow skills to diffuse between the parties and will, over the next several years, enable security to be truly baked in rather than bolted on.
- New respect for customer data. – Processing and holding customer data can no longer be seen as a business right, but rather as a privilege. Organizations must quickly learn to use customer data with appropriate care, protecting customer privacy and keeping personal data more secure.
- Start small, then go big. – When building new systems, it’s best to conceive of them as modules, each with security designed in from day one. In the past, many organizations would instead build monolithic systems, then apply a security “wrapper” after the design or development. But in an environment with thousands of mobile and IoT devices, that’s no longer sufficient. The newer, more effective approach involves building loosely coupled components, wherever possible, on a stateless/shared-nothing architecture with a zero trust mentality between modules.
- Prepare for failure. – With the further adoption of cloud computing, organizations no longer have total control over their computing or storage platforms. New risks are introduced, and some elements will fail. You can no longer try to design around these potential failures; instead, you must plan for them.
One powerful approach that requires a new cultural mind-set is known as resiliency engineering. This involves building systems so when one component goes down or is overwhelmed, its effect on the overall system is predictable.
A related approach, refined for distributed solutions by Netflix, is known as chaos engineering. Here, IT employees experiment against a working system daily by pushing unknown conditions, including shutting down on different assumptions, in the system to make sure continuous operations are possible. If not, the test group can see where the gaps are, and then improve the recovery automation.
Chaos engineering generally delivers better results than traditional site-oriented business-continuity testing. The latter is done under specific conditions, thereby failing to accurately mimic unexpected challenges.
Process is the second lane on the enterprise risk highway, relating to how an organization approaches its business processes. This might involve moving from ITIL to DevOps or other automation-friendly approaches. It could also mean integrating cloud providers that have security and privacy features built in.
That becomes especially important if the shift to cloud involves use of “serverless” computing environments. Moving workloads to the public cloud still requires you to manage the underlying cloud infrastructure. But with serverless, when you switch on a web service, you no longer have to worry about that infrastructure; that becomes the responsibility of the cloud provider, making it more important to select the right vendor.
Many cloud suppliers today offer highly resilient environments, but some risk will remain. Risk that evades even the best attempts at detection and prevention is known as “residual risk.” Fortunately, organizations have a new way to hedge their residual risk: cyber insurance.
When all else fails, cyber insurance can act as an organization’s final safety net, addressing residual risk. Payments from a cyber insurance policy could go to IT for restoring systems, to finance for reimbursing affected customers and to public relations for repairing the organization’s reputation.
Still, cyber insurance should not be considered a panacea. Like most insurance policies, it is part of the overall resiliency that organizations need. Traditional insurers enjoy sophisticated and time-proven tools, including actuarial tables, to help them assign and manage risk profitably. Cyber insurers are still gathering insights, adjusting offerings and introducing more tools to best assign risk and manage it.
Also, while an organization can transfer some risk with cyber insurance, it still can’t transfer responsibility. Diligence and simulation remain vital.
Technology is the third lane on the risk highway. Emerging technologies can present new risks, but they can also help address risk. Many top technology companies, for example, are using technologies to automate processes in a way that’s secure. Their best practices will become the common practices of organizations in all industries.
Machine learning, a subset of artificial intelligence (AI), has become a viable tool for threat detection because it can detect anomalies. For example, if an executive most often logs in from her office in London, then that’s her norm. But if one night that same executive logs in from Tokyo, that’s an anomaly. It could be harmless, but what if a cyber criminal is impersonating the executive and attempting to gain access to the network? Either way, it’s something to detect, check out and, if warranted, take action against.
Machine learning is critical because it addresses scalability. If you have a handful of mobile users and internet of things (IoT) and operational technology (OT) devices to monitor, you could handle the work with current staff. But it is more likely you have thousands of mobile users each with their own working patterns and locations (e.g., office workers, contractors, field workers, teleworkers) and each owning multiple devices and even more IoT and OT devices.
Suddenly, the task of establishing a norm for each user and device, watching for anomalies and then deciding which ones require preventive action moves beyond human capabilities. Machine learning can automate this process and keep a much tighter watch on who and what is allowed onto the network.
Indeed, one of the most important areas to address with technology best practices is identity management. In a world of hybrid clouds, proliferating devices and highly mobile users, the network becomes a “zero trust” environment where the identity of every user and device must be verified before access is granted. That’s because countless IoT devices, RPA software, bots and other automated devices are already banging on network doors, with many more coming soon.
A new vision for managed risk
Few organizations have achieved a fully transformed environment for enterprise risk. Yet the contour of this new environment is already becoming clear.
As noted, machine learning will play a central new role. This technology can automate an organization’s end-to-end response to security threats, from detection to response. Speed is important because early detection reduces the likelihood of further attacks. By orchestrating the organization’s responses to new vulnerabilities with automation, systems can recover from breaches quickly.
Security threats are growing faster than organizations are able to add specialists to thwart them, so organizations continue to find themselves shorthanded when attempting to manage this explosion of security incidents. Compounded by the widened scope of cyber-physical risks through the inclusion of IoT and OT systems, most organizations will feel deluged by the risk management activity of these concerns. The solution? Leveraging technology and services, including the cloud and automation tools along with managed security services.
Ultimately, the business needs a single, converged view of technology risk across both operational and security domains. Whether an application is taken down as a result of a failed cooler in a server farm or a criminal action, the impact on the business is similar. The incident response process is almost identical until the point at which an adversary is detected. With security skills becoming part of the wider IT skillset, and the dearth of pure-play security specialists, enterprises must employ a wider array of multi-skilled people to address this challenge. It’s the only viable way forward.
As we factor in all of the principles discussed, we then have to think about how to bring together our IT operations centers and security operations centers. We will start to generate joint risk management frameworks that give the business a single assessment of risk and associated levers to pull in reducing this risk.
How to get started?
Ready to start protecting your organization against the new security risks? The journey starts with four important steps:
- Create both digital transformation and enterprise security roadmaps. These two journeys are separate yet parallel.
- Create a security team for digital transformation. Security team members need to be a part of the digital transformation process and be able to articulate the security risks this journey will likely entail. Consider working with a trusted security partner who has broader expertise and experience to understand the risks and accelerate delivery of results while adhering to the enterprise’s risk appetite.
- Re-engineer processes to enforce proactive security. The combination of new privacy laws and new technologies will require most organizations to change the way they operate. Robust security will need to be proactively designed and built in from the start.
- Ensure that you have the right technologies. To achieve the desired transformation outcomes, you probably don’t have the right technology installed today. If that’s the case, your organization will need to bring in new tools designed to complement or replace existing technology.
In this way, organizations can implement a new approach to enterprise risk, one that ensures they have robust security from the very start. It’s also an approach that can protect against whatever new risks emerge whether that’s today, tomorrow or beyond.
This article was taken from Mohammad Shahir, Ph.D.‘s LinkedIn.
Photo by Markus Spiske on Unsplash.

 4.4
4.4